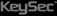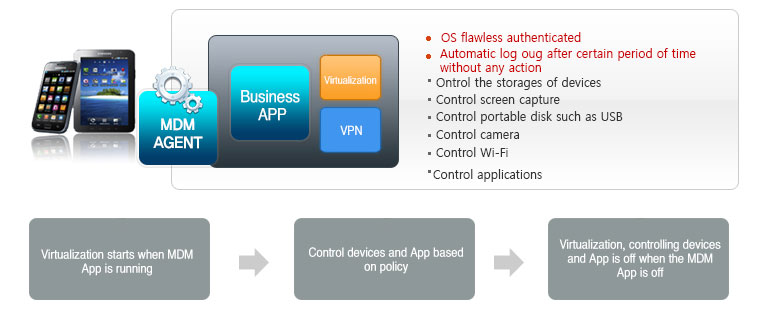


- Home > Products > MDM
-

-
Management of smart devices
- Smart device authentication and user authentication is performed
- Check the installation of smart devices in the MDM
- Check routing of smart devices
- OS check(iOS, Android, etc.)
- Support backup recovery for key records and information of smart devices 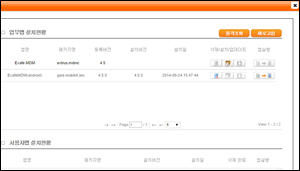
-
Control devices and apps
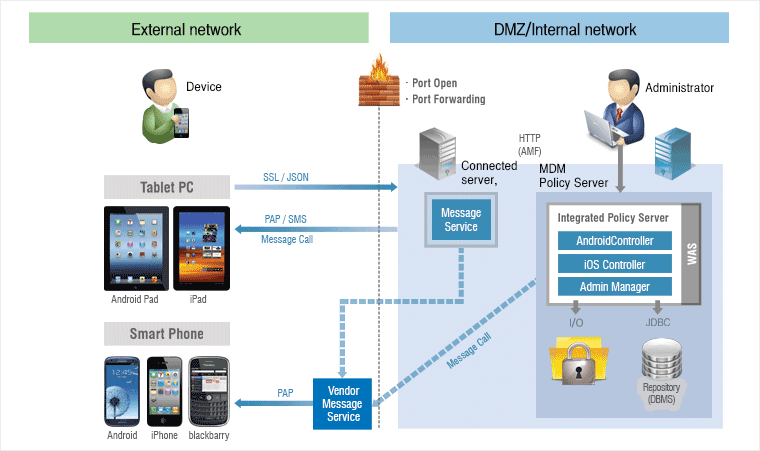
- Network Block (3G, Wi-Fi, Bluetooth, etc.)
- User apps restriction(camera, screen capture, recording, etc.)
- Business app installation and update management
- Prevent from deleting specific app and prevent forgery app
- Configure and manage work-related app
- Control the access of non-business apps and web browser 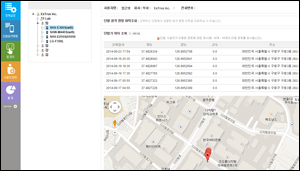
-
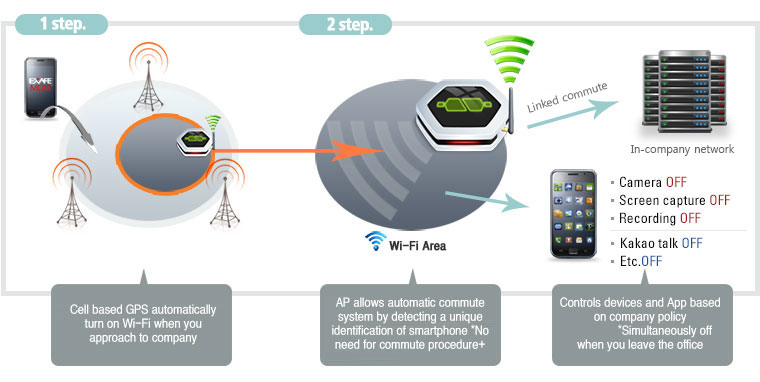
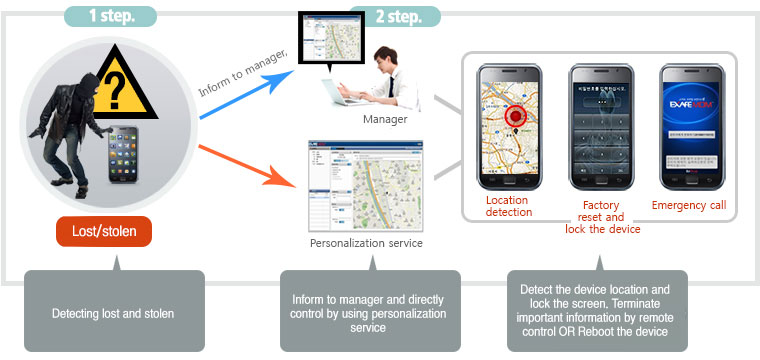
Correspond to Lost/stolen
- Lost / stolen status report
- GPS / WPS-based location lookup
- Remote control commands (factory reset, remote lock, etc.)
- Emergency call setup, search USIM information
- Set password forcedly and screen control
- Remote screen lock 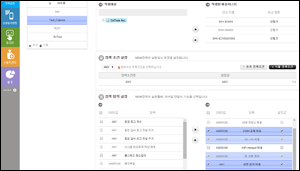
-
Condition-based security policy management
- Location-based Policy Management (Cell ID / GPS / WPS / Wi-Fi AP)
- Work-based policy management (access control system linked)
- User-Based policy Management (human resource DB link)
- Permission-based policy management (allow authoized app)
- Black list or White list based app management 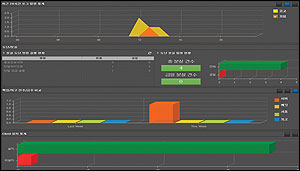
-
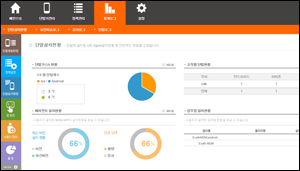
Statistics and reportingfunctions
- Lost / stolen status monitoring
- Backup and recovery status monitoring
- Client installation status monitoring
- Last log status monitoring
What is Mobile Device Management (MDM)?
MDM refers to a series of processes managing secured information of mobile devices, such as smartphones, tablets, and laptops.As corporations become more and more interested every day in the development of mobile office systems and work-related applications for public institutions using mobile devices, the management and security of mobile devices related to these matters are also a factor of interest.
Exafe MDM allows advanced prevention of personal or company information being exposed and/or misused.Mobile devices with secure transcription solutions and related security can be further enhanced.
|
Obey NIS Guidelines + Financial Supervisory Service’s
- Management through user authentication |
Mobile data protection system established
- Improvement of company’s liability through the configuration |